Breathing new life into Ruckus SmartZone 100 controllers (now EOL’d)
by firestorm_v1 on May.02, 2024, under Hardware, Investigative Dissassembly, Networking

Just like with most things, IT equipment has to evolve over time and wireless connectivity is one of those things. The company I work for decided to replace their aging Ruckus controllers and access points with Meraki access points (The decision was way above my paygrade) so that left a treasure trove of hardware behind that was destined for the waste bin. In this article, I’ll talk about the HA pair of the SmartZone100 controllers from Ruckus, their hardware capabilities, and what I plan on doing with my pair.
Pay no mind to the man behind the curtain…
As the preface said above, my company made the switch from the Ruckus SmartZone 100 controllers (in an HA pair) to Meraki which resulted in four boxes of APs (maybe about 50?) suddenly without a purpose. We ended up giving them away to employees who were all too eager to take them off our hands. The controllers on the other hand, were already in pretty bad shape. One of them was working fine, but the other had a failed disk. Add to the fact that they’re end-of-lifed and Ruckus wasn’t willing to send us a replacement hard drive meant that these were destined for the waste bin.
For sh*ts and giggles, I decided to crack one of them open and I was mildly surprised at what I saw. I halfway expected an ARM based processor or some similar device like what’s in Unifi’s controllers and network devices, but the hardware inside the SmartZone 100 was even better than I could expect.
As it ends up, the Ruckus SmartZone 100 controller runs a lot of commodity off the shelf hardware which means that it’s got more life to live than just a wireless controller if you are willing to put in the effort to make it.
Hardware Overview
The Ruckus SmartZone 100 controller has the following hardware features:
- Processor: Intel I7-3770 Quad-core processor at 3.40GHz
- RAM: 32GB DDR3 (in 4x8GB sticks)
- Networking: Four Intel i350 Copper Gigabit PCI Express Ethernet Adapters (front facing)
- Two front-facing USB ports
- One front-facing RJ-45 Serial port (Cisco console cable compatible, use 115200,n,8,1)
- Two internal SATA ports and one internal Molex port (for power)
- One hard drive mount bracket
- One 320GB Toshiba MQ01ABF032 SATA Hard Drive
- Integrated auto-ranging power supply
- Front panel status LEDs for Power and HDD access and link/activity for each NIC.
- A recessed reset switch
- A recessed F/D switch (For Ruckus, this would factory reset the appliance, it doesn’t appear to do anything with OPNsense).
- A “status” LED that blinks red. (In the Ruckus controller software, this would indicate the controller’s health.)
The 1U case is a specific-design case, but there is a lot of room for hardware modification if desired. It looks like this case or another product built on this case and motherboard may have supported PCI Express expansion, however the SmartZone100 did not have that additional hardware. A blank cover is fixed over where the expansion slot could have gone. Another blank cover is in front of the hard drive mount, indicating that a variant of this board may have offered externally accessible hard drive bays.
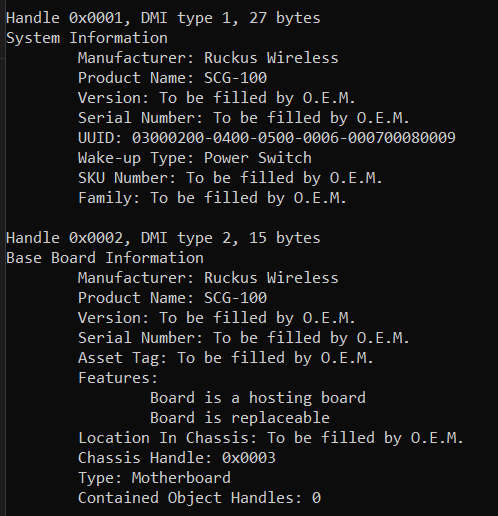
Online research into this motherboard including all numbers on various stickers and pcb silkscreen didn’t turn up anything. Additional searching with information returned by dmidecode was similarly fruitless. It was seen that a lot of the dmidecode entries were “to be determined” and “To be filled by OEM” as shown below:
Software Overview
Admittedly, I didn’t spend much time with the software. It appears that the controllers run CentOS 7 Linux, have grub as the boot loader, and for all intents and purposes are proprietary software running on a Linux platform. While I can’t edit the bootloader configuration (it appears to be password protected), I can mount the drive using another Linux system as a rescue host and examine the filesystem there. User logins exist for admin (from when they were in production) and there’s an enable password for “root” level access, they both are constrained to a proprietary Ruckus shell for administering the Ruckus wireless deployment. I’ve thought about rescuing the disk, then inserting another user with /bin/sh as their shell versus the Ruckus CLI.
Watch the Gotchas!
In my experimentation with these controllers, I found out that while there is a non-UEFI BIOS present, it does not have any known BIOS hotkey, so there weren’t any settings I could change. The controllers appeared to be configured to auto-detect the hard drive and then attempt to boot from it. If the hard drive doesn’t boot, then it falls back to PXE boot from each of the four interfaces on the machine. I attempted several times to get the machine to boot from a USB drive or a CDROM but ultimately gave up. The serial console on the front of the controller starts display from boot so all boot messages are captured, including the four Intel NICs trying to PXE boot. This may be able to be used as a recovery mechanism if the drive starts failing or may have been used as part of the OS installation and commissioning at the Ruckus factory.
On the front panel of the appliances, on the left-hand side, there is a F/D button that is supposed to factory reset the appliance if depressed for long enough, however I don’t believe that does anything in OPNsense. An annoyance is that the “status” LED on the left hand side will blink red because there’s no method to change the LED’s state. In the Ruckus software, the controller would set the LED according to one of several patterns indicating what’s going on with the appliance. This software doesn’t exist in OPNsense that I’ve found.
What to do… what to do?
When it came time to dispose of these controllers, one of the two machines had a failing hard drive so I knew that I would not be able to get the controller working in an HA pair unless I got really lucky with the data recovery. And even if I was successful, all of my Ruckus APs at home run Unleashed firmware (a semi-controllerless wireless management system). I really couldn’t justify running an entire controller just for four APs so getting the second unit running with “stock” Ruckus controller software disappeared as a goal pretty quickly.
Instead of a wireless controller pair, I decided to make them into OPNsense firewalls and build them out into a firewall HA pair. I threw a couple of 256GB SSDs into a test bed machine and installed OPNsense on them, set the root passwords, and then shut down the testbed and transplanted the hard drives into their new homes. Below is one of the machines’ system info dashboards.
OPNsense and beyond
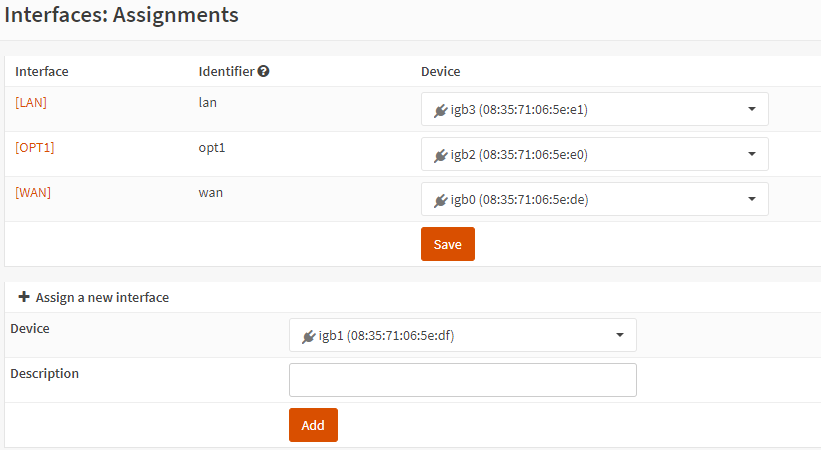
The two Ruckus controllers booted OPNsense without any issue from the SSDs I preinstalled. From the beginning, I was able to assign physical interface roles and set IP addresses and I was immediately off to the races. The four NICs in each controller shows up as igbX and the interface numbers match the interface labels on the front of the appliance (interface 1 is igb1 and so on). As shown in the screenshot below, I was able to get them set up quickly and into their respective roles.
Final thoughts and what’s next?
Well, for now, as stated before, I plan on setting these two appliances up as OPNsense firewalls, get them configured for high availability, and ultimately switch from a single pfSense machine (a Dell R210-II) to these two machines. I’ll have to give up the expansion 10G NIC that’s currently in my pfSense box that connects it to core, but to be honest, it’s overkill. I’ll never have more than a gigabit uplink anyway.
While it’s not *perfect*, it’s pretty darn close for a proprietary appliance converted to OPNsense. I look forward to running these for a very long time. At some point in the future, I’d like to get that status LED fixed, see if I can make the F/D switch do something, and maybe add more SSDs for a ZFS mirror in each appliance. I’ve already had situations where ZFS on the firewall has saved my rear end, and it would be almost trivial to add to the chassis.
If you’ve got an idea to do something similar, be aware that these controllers are still fetching a pretty penny on ebay. As of this writing, a SmartZone 100 is running about $300-600, and almost double that for the SZ controllers with 10G SFP+ cages. Note: I do not know if the SFP+ variant is supported by OPNsense, my controllers do not have the 10G option but it stands to reason that they would.
Happy Hacking!
FIRESTORM_v1